A quick tutorial to show how you can easily be more anonymous online.
Requirements
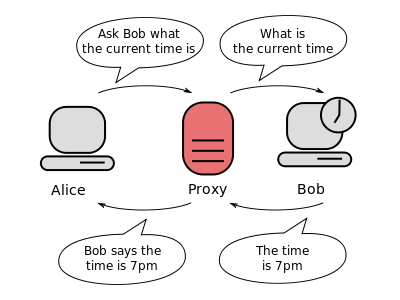
- Basic knowledge of what a proxy server is
- A Linux computer and basic knowledge of the terminal. (I’m using Ubuntu)
Okay if you’re ready let’s jump right in. You may want to start by checking what isn’t private there are a few ways to do this but for an easy way go to: DNS Leak Test
Disclaimer: Use at your own risk. This tutorial is for educational purposes and I don’t condone any illegal actions that one may be tempted to do with a newfound anonymity.
1. Install some tools
Type or copy/paste those commands in your terminal. (may be different if you’re not on a Debian based Linux distro)
sudo apt-get install tor
sudo apt-get install proxychainsTor is optional if you have some other services. (you can google for free proxies) Proxychains is the tool we’ll use.
2. Edit proxychains.conf
Once you have installed the tools we will need to setup proxychains. Edit the config file using the command below.
sudo nano /etc/proxychains.confThis will open a text editor in your terminal. Use the arrow keys to navigate. This is what we’ll do:
- enable dynamic chains
- disable strict chain
- enable proxy_dns
- add tor socks5
The # are comments to enable a setting you uncomment it ( remove the # ) and to disable just add a # For example enable dynamic chains, it should look like this:
dynamic_chainDo the above steps except for socks5 I’ll explain that below. After you changed the settings it should look something like this
dynamic_chain
#
# Dynamic - Each connection will be done via chained proxies
# all proxies chained in the order as they appear in the list
# at least one proxy must be online to play in chain
# (dead proxies are skipped)
# otherwise EINTR is returned to the app
#
#strict_chain
#
# Strict - Each connection will be done via chained proxies
# all proxies chained in the order as they appear in the list
# all proxies must be online to play in chain
# otherwise EINTR is returned to the app
#
#random_chain
#
# Random - Each connection will be done via random proxy
# (or proxy chain, see chain_len) from the list.
# this option is good to test your IDS :)# Make sense only if random_chain
#chain_len = 2# Quiet mode (no output from library)
#quiet_mode# Proxy DNS requests - no leak for DNS data
proxy_dnsThen scroll to the bottom you’ll see some things about proxylist, and examples. You should see something like:
[ProxyList]
# add proxy here ...
# meanwile
# defaults set to "tor"
socks4 127.0.0.1 9050Below that add the same information as the one above, but as a socks5:
socks5 127.0.0.1 9050Socks5 is just the best version. If you have your own proxies that you found elsewhere this is where you add them.
Now save by pressing:
CTRL + O then ENTER
Exit by pressing: CTRL + X
Finally, make sure tor service is running by doing:
service tor statusCheck if it’s running then press CTRL + C to exit. If it’s not running type:
service tor startThe moment of truth now. Use it to open Firefox and test if it’s working by entering this:
proxychains firefox https://www.dnsleaktest.com/See if it shows a different location /IP address and do a test.
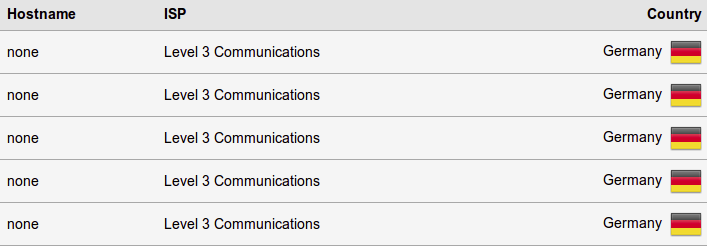
It works! I teleported to Germany!
Original article :
How to setup a proxy server on Linux (free)